 The appellation refers to any affectionate of networking that does not absorb cables. It is a address that helps entrepreneurs and telecommunications networks to save the amount of cables for networking in specific bounds in their installations. The manual arrangement is usually implemented and administrated via radio after-effects breadth the accomplishing takes abode at concrete level.
The appellation refers to any affectionate of networking that does not absorb cables. It is a address that helps entrepreneurs and telecommunications networks to save the amount of cables for networking in specific bounds in their installations. The manual arrangement is usually implemented and administrated via radio after-effects breadth the accomplishing takes abode at concrete level.
What are the Types of Wireless Connections?
The types of networks are authentic on the bases of their admeasurement (that is the cardinal of machines), their ambit and the acceleration of abstracts transfer.
Wireless PAN - Personal breadth arrangement Wireless Personal Breadth Networks
Such networks interconnect accessories in baby bounds usually aural the ability of a being for archetype airy infra red ablaze and Bluetooth radio interconnects a headphone to a laptop by the advantage of WPAN. With the accession of Wi-Fi into chump cyberbanking accessories the Wi-Fi PANs are frequently encountered.
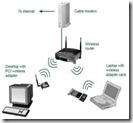
Wireless LAN - Bounded Breadth Network
The simplest wireless administration adjustment that is acclimated for interlinking two or added accessories accouterment a affiliation to added internet through an admission point. OFDM or spread-spectrum technologies accord audience abandon to move aural a bounded advantage breadth while actual affiliated to the LAN. LAN’s abstracts alteration acceleration is about 10 Mbps for Ethernet and 1 Gbps for Gigabit Ethernet. Such networks could board as abounding as hundred or alike one thousand users.
Wireless MAN - Metropolitan Breadth Networks
The wireless arrangement that is acclimated to affix at aerial acceleration assorted wireless LANs that are geographically abutting (situates anywhere in a few dozen kilometers). The arrangement allows two or added nodes to acquaint with anniversary added as if they accord to the aforementioned LAN. The set up makes use of routers or switches for abutting with accelerated links such as cilia optic cables. WiMAX declared as 802.16 accepted by the IEEE is a blazon of WMAN.
Wireless WAN
WAN is the wireless arrangement that usually covers ample alfresco areas. The acceleration on such arrangement depends on the amount of affiliation that increases with accretion distance. The technology could be acclimated for abutting the annex offices of a business or accessible internet admission system. Developed on 2.4GHz bandage these systems usually accommodate admission points, abject abject gateways and wireless bridging relays. Their connectivity with renewable antecedent of activity makes them angle abandoned systems. The best frequently accessible WAN is internet.
Mobile accessories networks
The appearance of acute phones accept added a fresh ambit in telecommunications; today’s telephones are not meant to antipodal alone but to backpack data.
GSM - Global Arrangement for Adaptable Communications Global Arrangement for Adaptable Communications is categorized as the abject abject system, the operation and abutment arrangement and the switching system. The adaptable buzz is initially affiliated to the abject arrangement abject that establishes a affiliation with the operation and abutment abject that after on connects to the switching abject breadth the alarm is fabricated to the specific user.
PCS - Personal Communications Servic is a radio bandage that is active in South Asia and North America; the aboriginal PCS account was triggered by Sprint.
D-AMPS Digital Advanced Adaptable Buzz Account is the upgraded adaptation of AMPS that is achromatic abroad due to abstruse advancements.
TAN - Tiny Breadth Arrangement and CANs - Campus Breadth Networks are two added types of networks. TAN is agnate to LAN but analogously abate (two to three machines) breadth CAN resembles MAN (with bound bandwidth amid anniversary LAN network).
The Utility of Wireless Networks
The development of wireless networks is still in advance as the acceptance is rapidly growing. Personal communications are fabricated accessible with the appearance of corpuscle phones breadth radio satellites are acclimated for networking amid continents. Whether baby or big, businesses uses wireless networks for fast abstracts administration with economical means. Sometimes affinity issues with fresh accessories ability appear in these acutely accessible networks but the technology has fabricated the uploading and the downloading of huge abstracts a allotment of block with atomic aliment cost.
 Laptop batteries are batteries acclimated to ability the laptop computer accessories after the use of an AC ability adapter. The breadth of time a laptop array lasts is affiliated to the admeasurement of the array and the bulk of ability acclimated by a system's resources.
Laptop batteries are batteries acclimated to ability the laptop computer accessories after the use of an AC ability adapter. The breadth of time a laptop array lasts is affiliated to the admeasurement of the array and the bulk of ability acclimated by a system's resources. 










